Linux Tutorial: SSH Forwarding & SSH Tunneling
Level up your ssh skills by understanding how to use the config file, ssh agent forwarding, and tunneling.

Contents
Introduction
This article is to enlighten you on some of the cool things you can do with SSH.
Well be focussing on two methods of connecting: Forwarding and Tunneling.
I'll also be teaching you the importance of the config file, which will help you speed up your connecting.
If you're new to Linux or need a refresher then click here for more articles.
SSH Config File
It's likely that you don't have a config file, or maybe you do but you have no idea what it does.
This is a normal text file located in your .ssh directory called config, and knowing how to use it can save you a lot of time in the future.
You can use it to map the parameters you would use to connect to an endpoint to a single keyword. This will save you from writing out the entire ssh command.
Lets take a look at an example configuration
Host <custom_name>
Hostname <hostname>
User <username>
Port <port_number>
Identityfile <path_to_private_key>config template
Note: the Identityfile parameter is optional - if you don't have a private key configured to your SSH hostname then you can leave this parameter out.
This config allows you to condense
ssh -i <path_to_private_key> <username>@<hostname> -P <port_number>
into
ssh <custom_name>
This saves you the trouble of having to remember the parameters plus you can use this anywhere in the linux filesystem.
For more information, go here.
SSH Agent Forwarding
Below, I am connecting to a bastion server on a public subnet in my VPC. I then try to connect to my Kali instance running in a private subnet, but fail because I'm not using the private key.
The private key is located on my local .ssh directory.
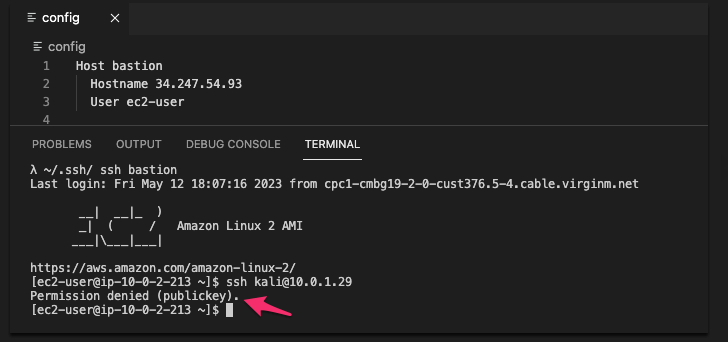
How would you overcome this problem?
If you're thinking, make a copy of the private key and use scp to copy it onto the bastion, and you're also thinking that sounds incredibly insecure - and just a massive hassle to pull off - then you're going to love agent forwarding.
In order to connect to a machine via ssh, you need an ssh agent running and listening on a port (usually port 22).
The agent has the ability to save your private keys to a "keychain".
This allows you to effectively take the keys with you when you connect to another machine without actually copying and pasting the key to a new location.
To add the key to take with you, use
ssh-add <private_key>

Now that you have the key, try ssh-ing onto your server again.
This time, use the -A flag.
ssh -A ... will let you forward your local ssh agent.
If we try to connect again...
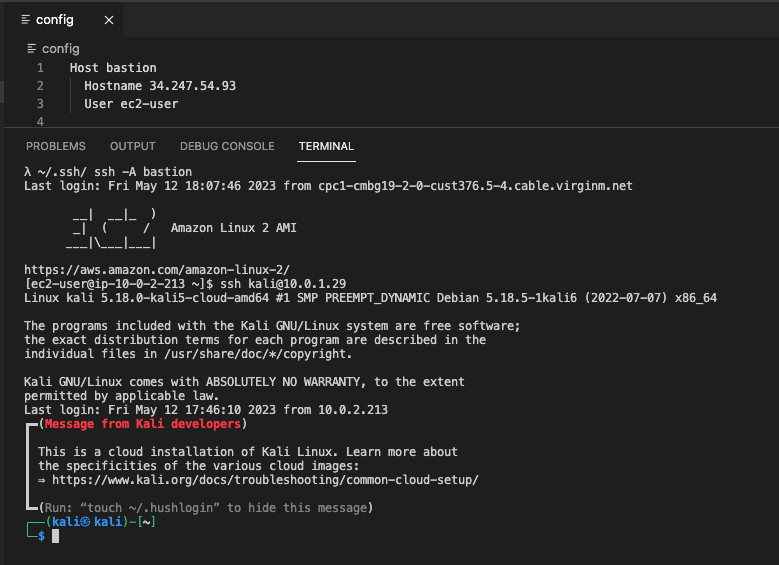
... We're in!
SSH Tunneling
Same scenario as before, only this time we're going to bypass the bastion and connect directly from our local machine to the Kali using ssh tunneling.
We still have to use the bastion to establish a tunnel to the Kali from our local.
This one is a little tricky to explain, so bear with me.
To create a tunnel from your local to you target instance you will need the -L flag.
With it you can connect a port from the local machine, say port 2222, to the ssh port of your target machine, port 22.
The syntax might look weird but it's pretty intuitive when you know what it means.
ssh -L <local_port>:<target_host>:<target_host_port> ...
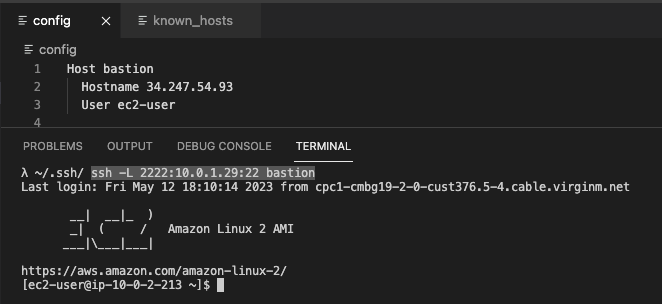
In the example above, I'm connecting my localhost to the target via ports 2222 and 22 respectively.
<target_host> can be either a hostname or a ip address.
There's no visible indication that the tunnel has been established, you just get what looks like a normal ssh connection.
But that's a good indicator that it work.
Now, if we open a different tab and use ssh to connect to our localhost on port 2222...
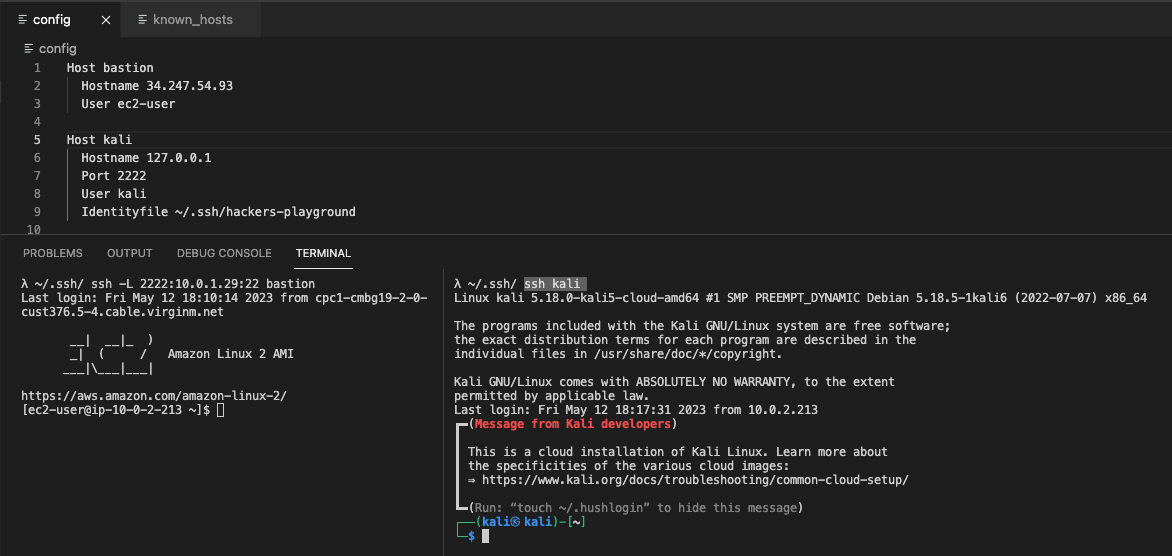
... It connects!
Remember, the config file simplifies the command. What I've effectively run is
ssh -i "~/.ssh/hackers-playground" kali@127.0.0.1 -P 2222
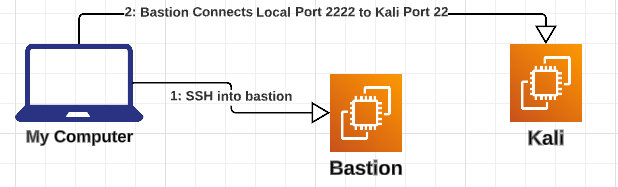
The bastion acts as an intermediate which allows a connection between the two machine.
