Linux Firewall: How to use Iptables
Fortify your system against digital threats with the Linux Firewall tool, iptables.

A Firewall is one of the key security measures to secure your network.
Linux has a few options available for user that are crucial to securing their system without the cost associated with commercial products.
If you're reading this then you're probably already familiar with the concept of a Firewall. Here, you'll learn what it is and how it really work.
A firewall is a system that is configured to block certain types of traffic on the network.
There are many flavours of firewalls. Most of us are used to the software variety (AVG, McAfee, etc...), but there are dedicated hardware that sits in between a user and the client system. They stop malicious traffic from entering the client system in the first place.
There's also the web-based solution for HTTP traffic called Web Application Firewalls, or WAF.
Here, you will be learning about the built-in firewall utility for Linux, Iptables.
Iptables
Iptables consist of basic structures known as Tables, Chains, and Targets.
The hierarchy of iptables is as follows: A Table contain multiple Chains, which is just a set of Rules.
Table = [
Chain1 = [
Rule1,
Rule2,
Rule3
],
Chain2 = [
Rule4,
Rule5
]
]Tables
There are 4 built-in tables: Filter, NAT, Mangle, and RAW
- Filter Table - Default if no other table is specified. It has the following built-in Chains:
- INPUT Chain - For inbound traffic for the network
- OUTPUT Chain - Outbound traffic generated locally.
- FORWARD Chain - For packets being routed through the local network
- NAT Table
- PRE-ROUTING Chain - Alters packets before routing
- POST-ROUTING Chain - Alters packets after routing
- OUTPUT Chain
- Mangle Table
- PRE-ROUTING Chain
- OUTPUT Chain
- FORWARD Chain
- INPUT Chain
- POST-ROUTING Chain
- Raw Table
- PRE-ROUTING Chain
- OUTPUT Chain
Targets
When a packet meets the condition of a rule, it triggers one of a set of specific actions known as Targets.
The Target can be one of these special values:
- ACCEPT - Allows the packet to pass through the Firewall
- DROP - Firewall drops the packet
- REJECT - Drops packet and sends an error
- RETURN - Stop traversing current chain and continue at the next rule of the previous (calling) chain
Creating Rules
Let's create a rule that blocks any packets coming from 192.168.0.101.
There are a few important flags needed:
-A- Appends to chain-D- Deletes from chain-L- Lists rules in chain-s- Source IP-j- Target
Syntax example
sudo iptables -A <chain> -s <ip> -j <Target>sudo iptables -A INPUT -s 192.168.0.101 -j DROPYou can apply the rule to the entire subnetwork by replacing the ip with a CIDR (192.168.0.101 -> 192.168.0.0/24).
Accept TCP connection to this website? Use -p to specify protocols and -d to specify the destination.
sudo iptables -A OUTPUT -p tcp -d www.nullslashdev.com -j ACCEPTDeleting a Rule
Let's assume you're trying to cut down on your use of Youtube.
You write a rule into the Filter table to block access to www.youtube.com.
Before reading further, try to come up with the command yourself. Reread any parts or do your own research if you need to. It's good practice.
If you're all set, lets keep going.
To clarify, we want to append a new rule to the filter table to block traffic to www.youtube.com.
sudo iptables -t filter -A OUTPUT -d www.youtube.com -j DROPAs you can see from the screenshot below, the rule was added to the Filter table.
You can view the active rules from each table using the -S flag.
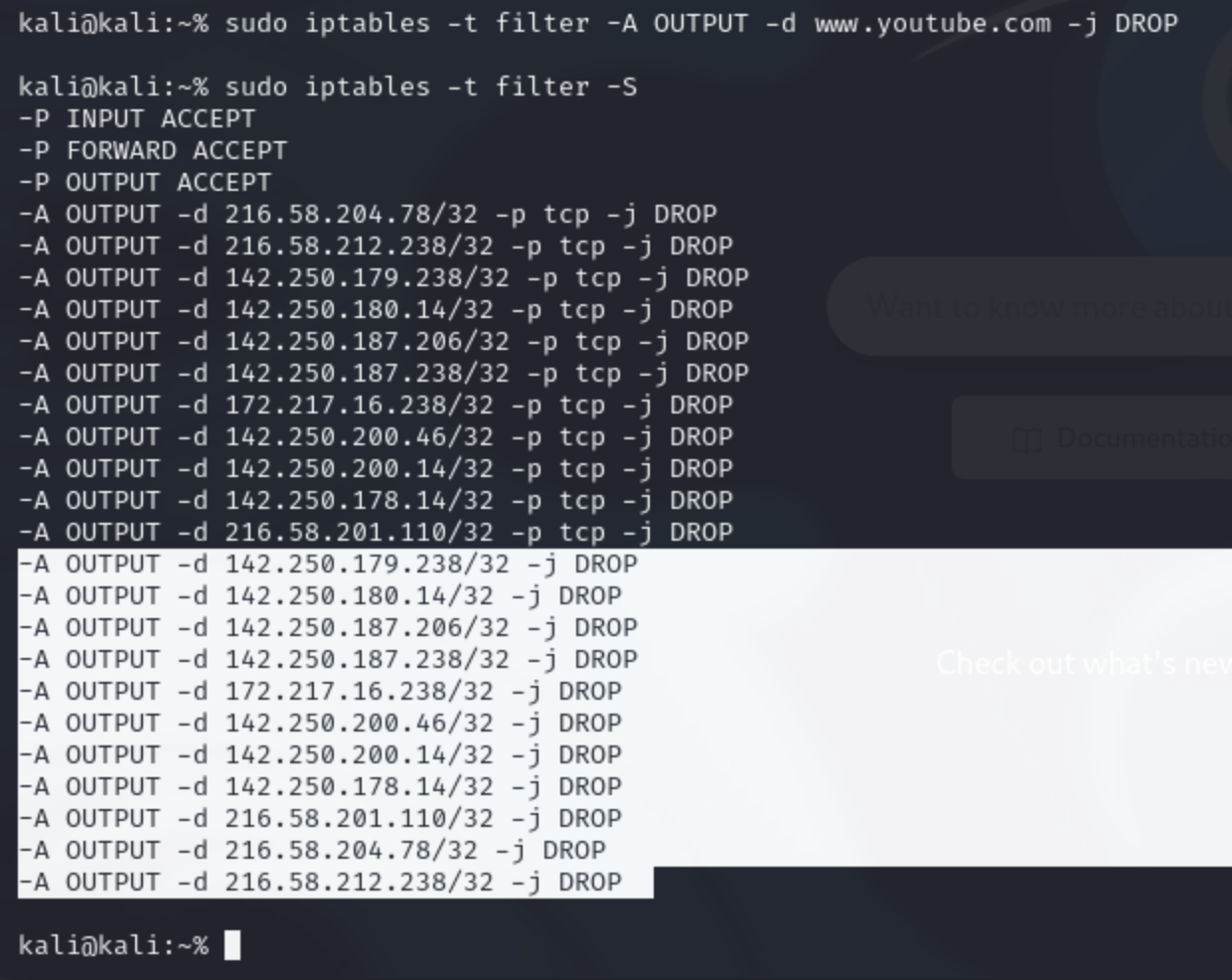
You might be wondering why there's so many rules that were added.
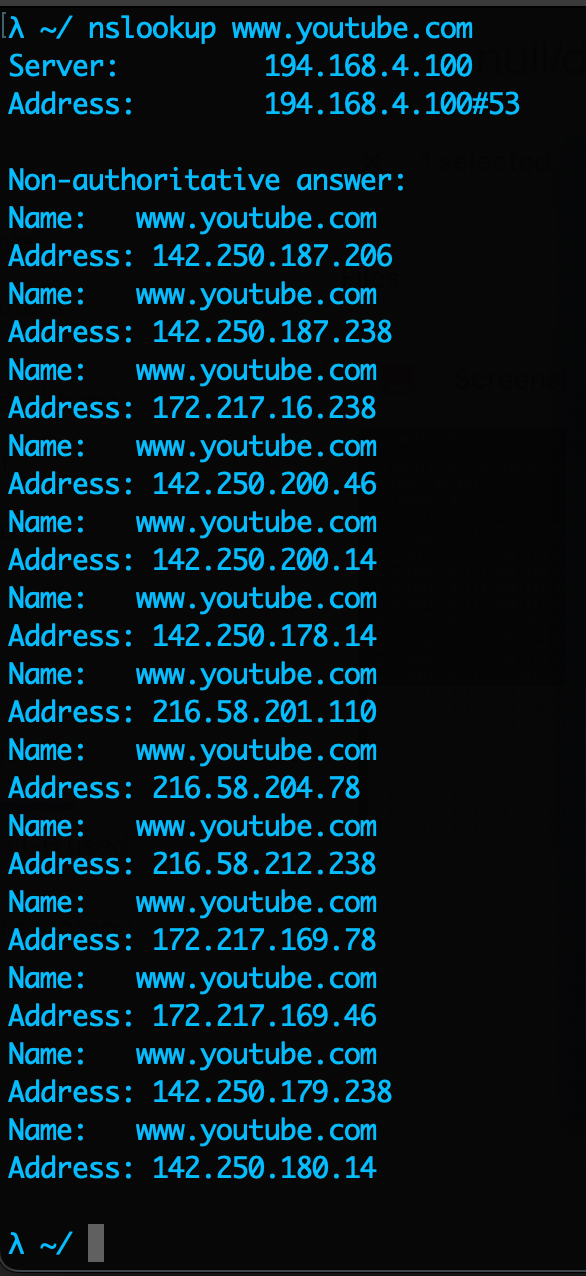
This is because when a rule is added, iptables does a DNS lookup to find all the IPs associated with the specified website.
If you were to use nslookup www.youtube.com then you would find the same IPs the were highlighted above.
Now that the rule is added, notice what happens when navigating to youtube.com
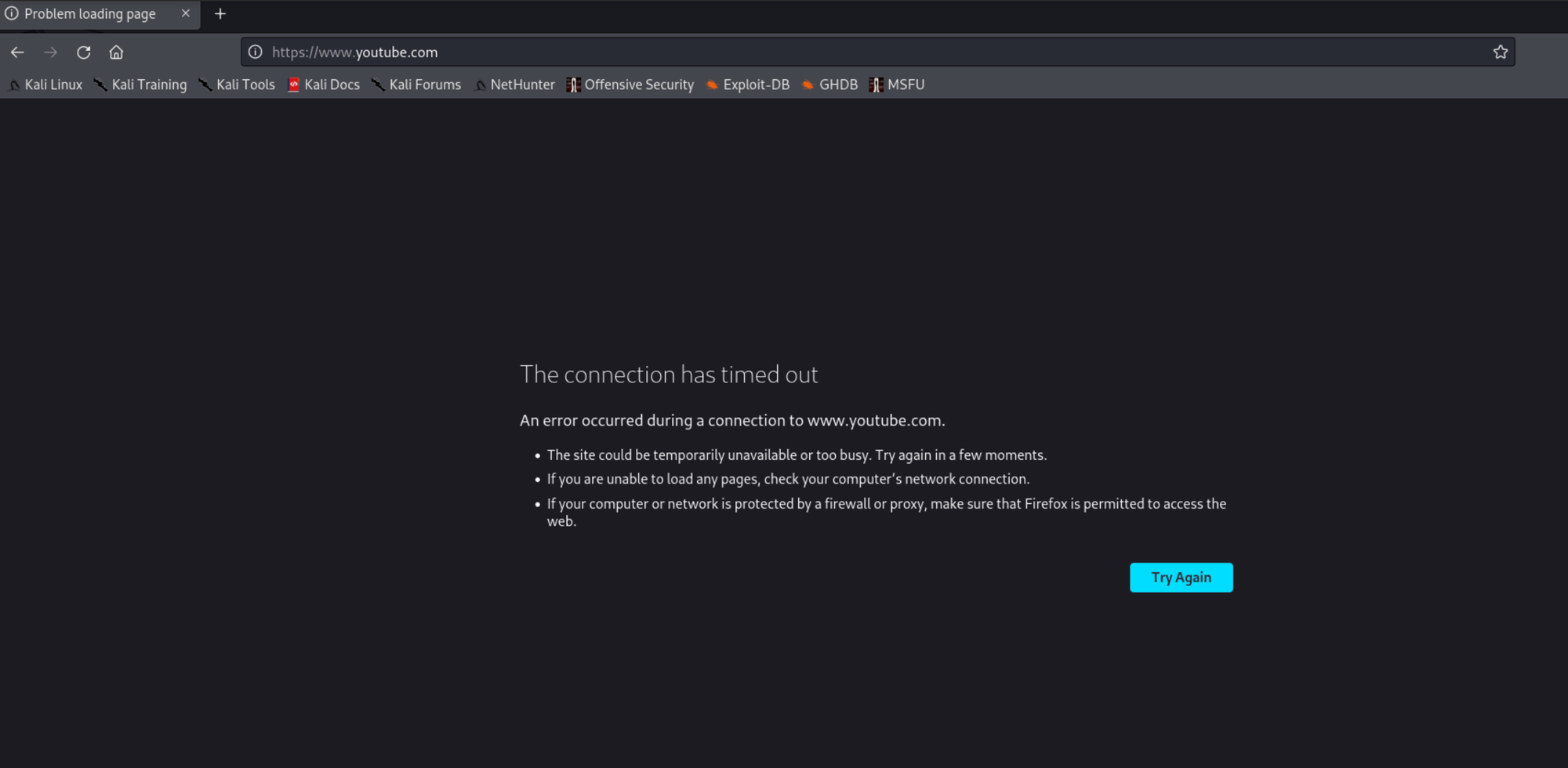
The connection has timed out. The rule works perfectly. Good thing (as of writing) I don't have any youtube tutorials, otherwise you'd be missing out. With that, let the detox begin.
Removing a Rule
Now imagine yourself going cold turkey. Time to get back access to the tube.
Lets look at the rules again
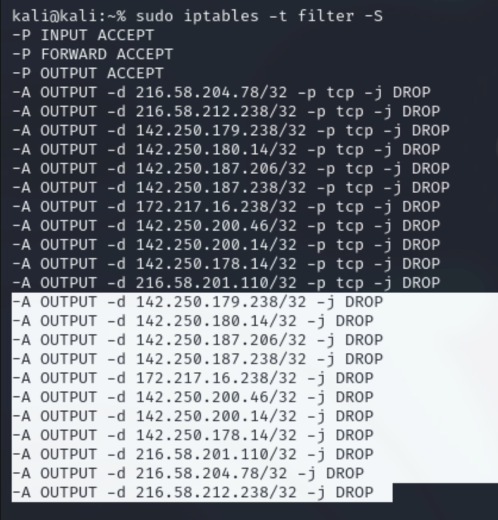
In order to ensure you can binge the tube again, you need to drop all of highlighted rules. This is done using the -D (delete) flag in combination with other flags.
For now lets try and delete one of these rules. You can specify which one using line numbers.
If you use --line-numbers in conjunction with the -L flag then you can you can get the index number for any rule.
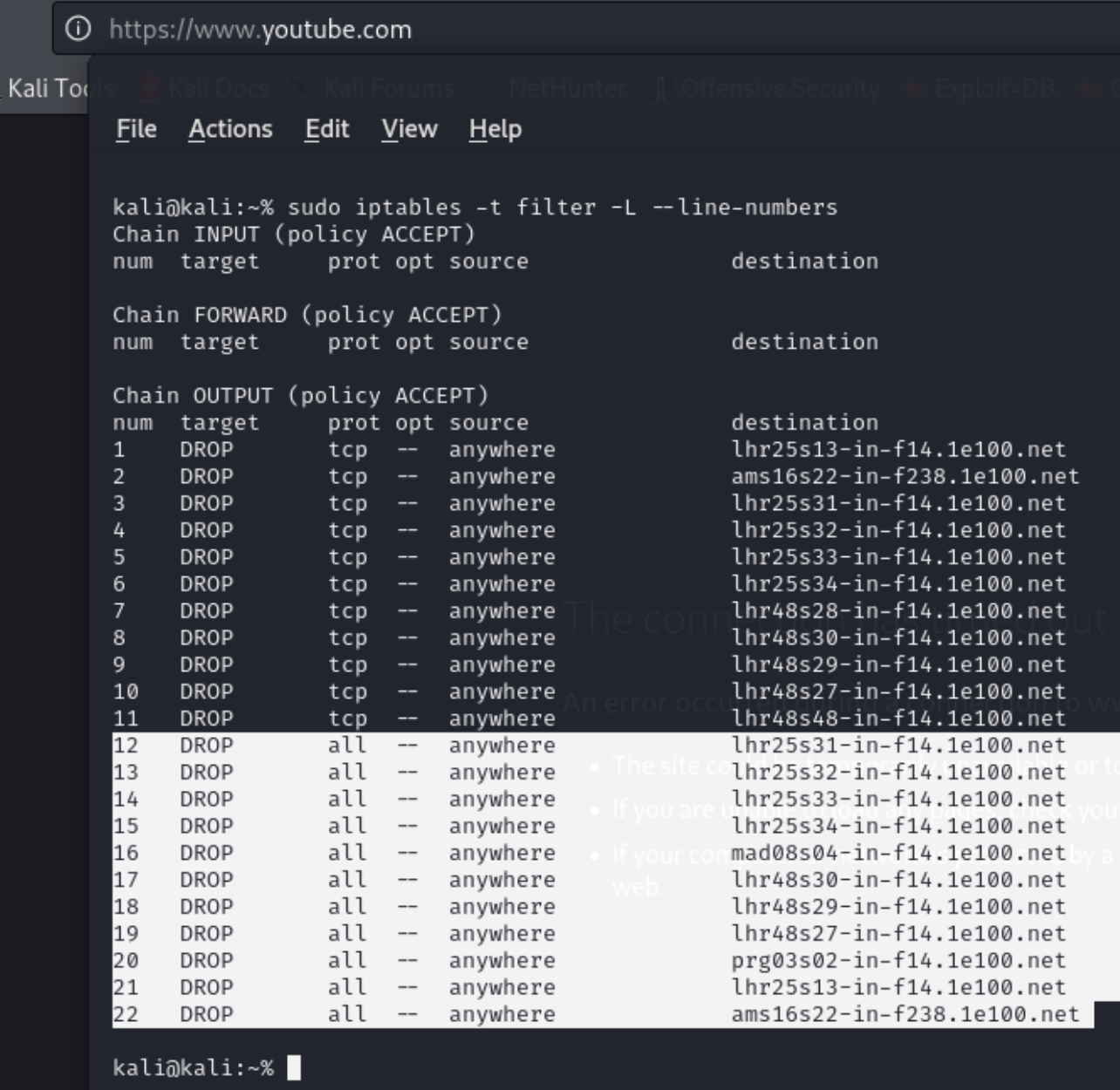
Lets drop the last rule (22). To do this you need to specify the chain and the line number:
sudo iptables -t filter -D OUTPUT 22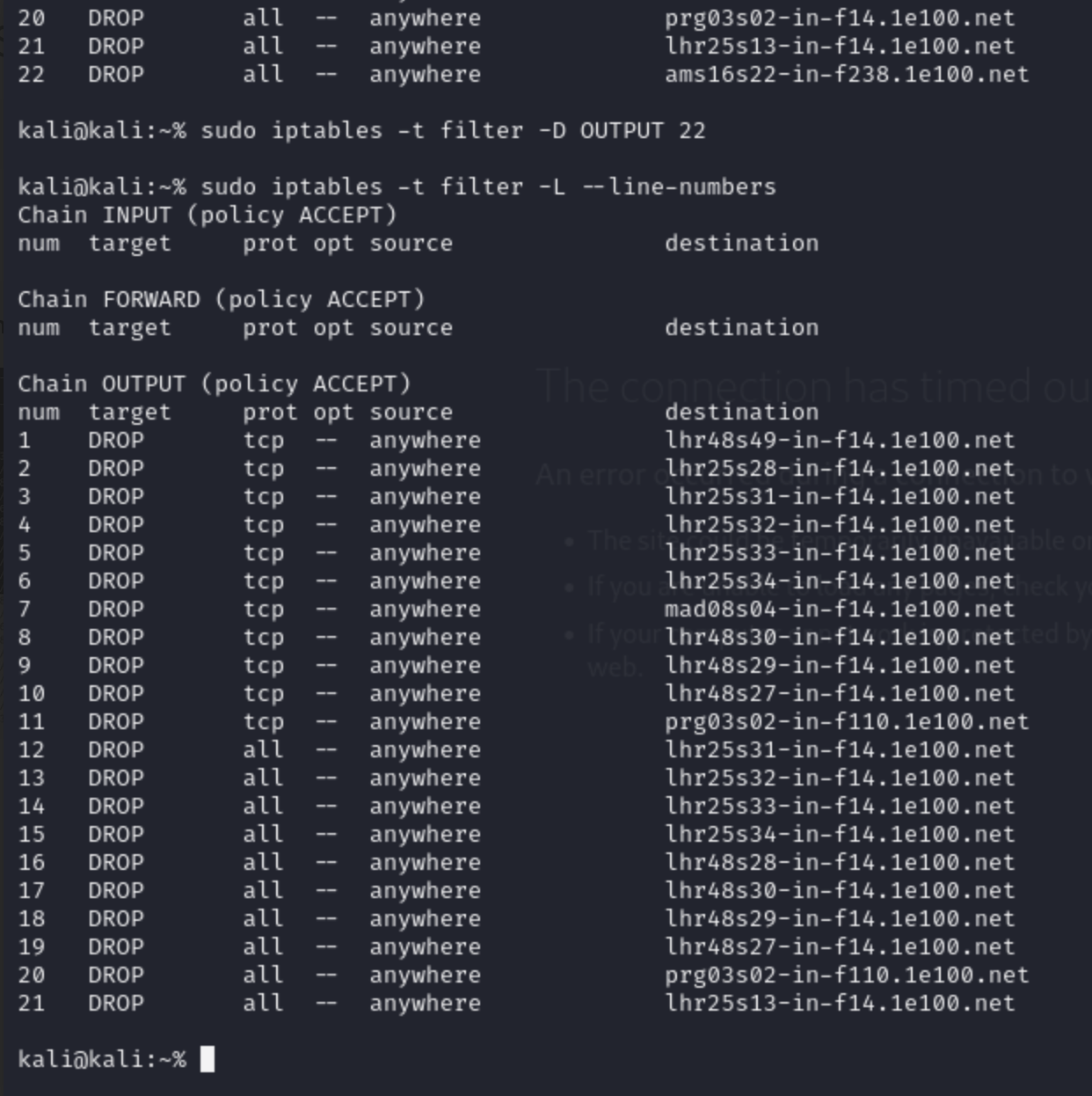
As you can see, there is now only 21 rules. We can do this for each rule individually, but there is a faster way.
This is done using the flush flag, --flush or -F
Before doing this, change the default policy for every built-in chain to ACCEPT to avoid getting shut out via ssh with
sudo iptables -P INPUT ACCEPT
sudo iptables -P FORWARD ACCEPT
sudo iptables -P OUTPUT ACCEPT
Using the flush flag removes all rules in a specified chain. If nothing is specified, then all chains in the default (filter) table will be removed, so be careful how you use it
To remove all the rules in the OUTPUT chain (including the rules for TCP) use
sudo iptables -t filter -F OUTPUT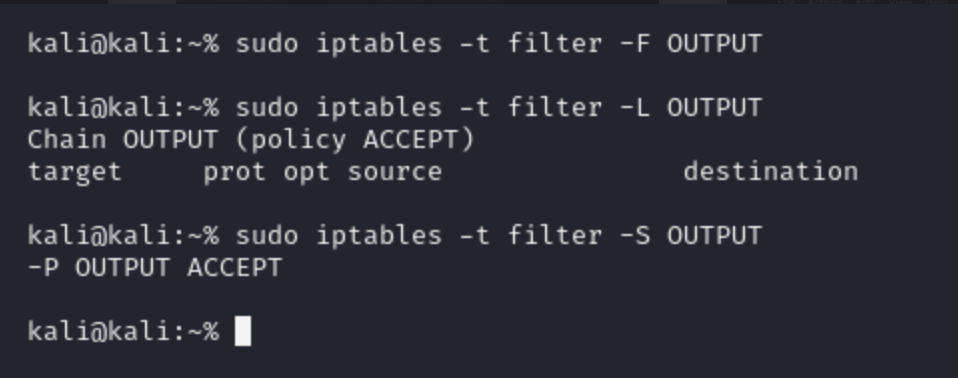
Now if we try and reload Youtube:
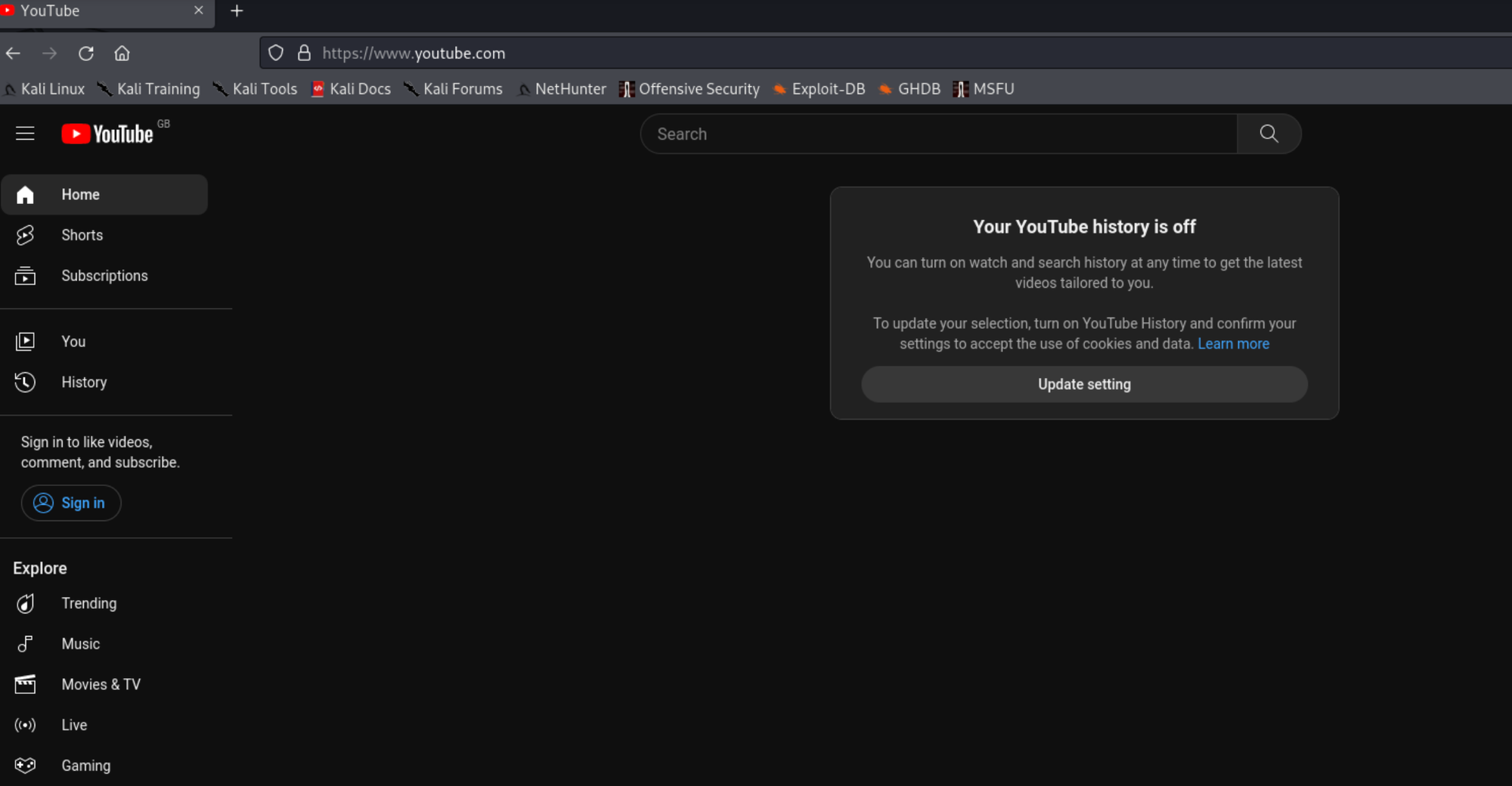
We can now reach the website again (or, at least, you should... I apparently have to update my history settings).
Final Thoughts
Iptables has a successor that is supposed to replace it along with ip6tables, arptables, and eatables.
It's called nftables and you can read more about it here.
However, the knowledge gained here isn't useless as even the newer technologies are built upon the same underlying concepts.
Nftables functions using tables, chains, and rules, so now you will find it easier to learn it, if you so choose.
Even if you don't, iptables is still a very functional firewall.
With enough practice you can build your own firewall that can rival commercial products.
